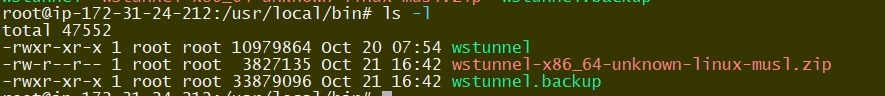
之前介绍的「wstunnel开源应用」近日接连发布了7.0 rc1、rc2以及7.0、7.1、7.1.1版本,终于提供了tar包,无需再安装unzip。命令行参数有所调整,透过参数也会发现程序功能有相应的增加,但作者目前尚未给出具体用例说明和参考。Rust重构后,二进制可执行文件(下图为7.0)的大小收缩是必然的,相较6.0缩小近70%。同时,代码效率提升也是肯定的,但隧道性能是否会同步提升尚且不得而知。
考虑到测试性或尝试性部署需求,新手如果还按照6.0的命令行写法就会报错了,因此,本文就服务端和客户端变化作摘要记录。
1.最小化应用
以下为docker镜像下载方法,以及wstunnel 7最小化应用的命令行,尖括号包裹的内容需替换。
#docker镜像下载 docker pull ghcr.io/erebe/wstunnel:v7.1.0 #Linux服务端 /path/to/wstunnel server wss://0.0.0.0:<server_port> #windows客户端 \path\to\wstunnel.exe client -L socks5://<socks_port> wss://<server_ip>:<server_port>
2.服务端
服务端及客户端启动分别采用server或client指定,“server”代替了“--server”。同时,最主要的变化在于增加了对linux下socket SO_MARK标记的支持。完整的命令与参数如下:
Usage: wstunnel server [OPTIONS] <ws[s]://0.0.0.0[:port]>
Arguments:
<ws[s]://0.0.0.0[:port]> Address of the wstunnel server to bind to
Example: With TLS wss://0.0.0.0:8080 or without ws://[::]:8080
Options:
--socket-so-mark <INT>
(linux only) Mark network packet with SO_MARK sockoption with the specified value.
You need to use {root, sudo, capabilities} to run wstunnel when using this option
--websocket-ping-frequency-sec <seconds>
Frequency at which the server will send websocket ping to client.
--websocket-mask-frame
Enable the masking of websocket frames. Default is false
Enable this option only if you use unsecure (non TLS) websocket server and you see some issues. Otherwise, it is just overhead.
--restrict-to <DEST:PORT>
Server will only accept connection from the specified tunnel information.
Can be specified multiple time
Example: --restrict-to "google.com:443" --restrict-to "localhost:22"
--restrict-http-upgrade-path-prefix <RESTRICT_HTTP_UPGRADE_PATH_PREFIX>
Server will only accept connection from if this specific path prefix is used during websocket upgrade.
Useful if you specify in the client a custom path prefix and you want the server to only allow this one.
The path prefix act as a secret to authenticate clients
Disabled by default. Accept all path prefix
--tls-certificate <FILE_PATH>
[Optional] Use custom certificate (.crt) instead of the default embedded self signed certificate.
--tls-private-key <FILE_PATH>
[Optional] Use a custom tls key (.key) that the server will use instead of the default embedded one
-h, --help
Print help
3.客户端
客户端取消了“-D”或者说是合并了“-D”、“-L”为“-L”。最主要的是增加了服务端验证选项,默认false,自定义sni在6.0中已支持。
Usage: wstunnel client [OPTIONS] <ws[s]://wstunnel.server.com[:port]>
Arguments:
<ws[s]://wstunnel.server.com[:port]> Address of the wstunnel server
Example: With TLS wss://wstunnel.example.com or without ws://wstunnel.example.com
Options:
-L, --local-to-remote <{tcp,udp,socks5,stdio}://[BIND:]PORT:HOST:PORT>
Listen on local and forwards traffic from remote. Can be specified multiple times
examples:
'tcp://1212:google.com:443' => listen locally on tcp on port 1212 and forward to google.com on port 443
'udp://1212:1.1.1.1:53' => listen locally on udp on port 1212 and forward to cloudflare dns 1.1.1.1 on port 53
'udp://1212:1.1.1.1:53?timeout_sec=10' timeout_sec on udp force close the tunnel after 10sec. Set it to 0 to disable the timeout [default: 30]
'socks5://1212' => listen locally with socks5 on port 1212 and forward dynamically requested tunnel
'socks5://1212?socket_so_mark=2' => each tunnel can have the socket_so_mark option, cf explanation on server command
'stdio://google.com:443' => listen for data from stdio, mainly for `ssh -o ProxyCommand="wstunnel client -L stdio://%h:%p ws://localhost:8080" my-server`
--tls-sni-override <DOMAIN_NAME>
Domain name that will be use as SNI during TLS handshake
Warning: If you are behind a CDN (i.e: Cloudflare) you must set this domain also in the http HOST header.
or it will be flagged as fishy and your request rejected
--tls-verify-certificate
Enable TLS certificate verification.
Disabled by default. The client will happily connect to any server with self signed certificate.
-p, --http-proxy <http://USER:PASS@HOST:PORT>
If set, will use this http proxy to connect to the server
--http-upgrade-path-prefix <HTTP_UPGRADE_PATH_PREFIX>
Use a specific prefix that will show up in the http path during the upgrade request.
Useful if you need to route requests server side but don't have vhosts [default: morille]
--http-upgrade-credentials <USER[:PASS]>
Pass authorization header with basic auth credentials during the upgrade request.
If you need more customization, you can use the http_headers option.
--websocket-ping-frequency-sec <seconds>
Frequency at which the client will send websocket ping to the server. [default: 30]
--websocket-mask-frame
Enable the masking of websocket frames. Default is false
Enable this option only if you use unsecure (non TLS) websocket server and you see some issues. Otherwise, it is just overhead.
-H, --http-headers <HEADER_NAME: HEADER_VALUE>
Send custom headers in the upgrade request
Can be specified multiple time
-h, --help
Print help
4.其他
不同于HTTP可以使用Basic Auth方法为服务器增加屏障以避免被滥用,Websocket并没有标准化的客户端验证方法支持。所以,可以通过添加头(Header)信息的方式进行客户验证。在wstunnel中就是使用http-upgrade-path-prefix选项来进行指定。
#Linux服务端 /path/to/wstunnel server --restrict-http-upgrade-path-prefix <string> wss://0.0.0.0:<server_port> #windows客户端 \path\to\wstunnel client --http-upgrade-path-prefix <string> -L socks5://<socks5_port> wss://<server_ip>:<server_port>
wstunnel简单到爆,但也可以有高级的用法,以6.0为例,比如以下一行命令就是将wss隧道出口流量转发给本地51820端口。
wstunnel -s wss://0.0.0.0/ --restrictTo 127.0.0.1:51820
再比如下一行命令是在本地监听udp 51820端口并经tcp 2185端口进入对端为your-remote-host的隧道。
wstunnel --udp -L 127.0.0.1:51820:127.0.0.1:2815 wss://<your-remote-host>:443
相信有人会对自己一直相信乃至痴迷的“技术”或“工具”产生疑问,没有疑问,注定是韭菜。
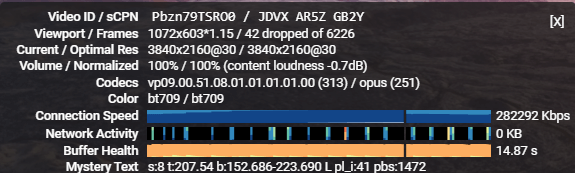
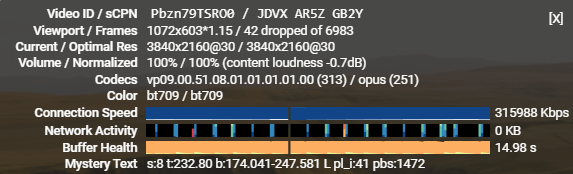
Rust重构后的wstunnel如果性能能够和Rust的代码效率相一致,是可以作为主力工具使用的,也包括渗透测试领域。以下仅仅是记录了Youtube的统计信息,无比较,只能说明“输出”稳定:CMCC线路、sg节点,稳定25万以上。
当然,目前的大小即便进行平台优化恐怕也很难在仅8M闪存的OpenWRT上安装了,尽管最新版本还提供了新的armv7二进制文件,但大多数人需要的是apk包,并不是所有安卓设备都可以root、也不是所有人都有能力root安卓设备,更多的人根本就没有意愿root设备。websocket /wbsocket secure是标准化的,无论是c、c++、go、python等都有成熟的库,开发门槛并不高。











文章评论